Storswift
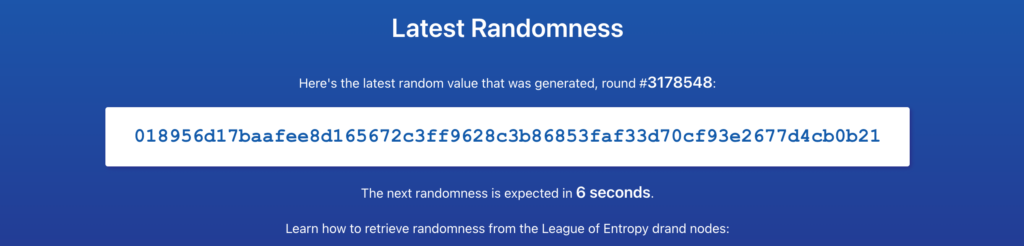
Verifiable, unpredictable and unbiased random numbers as a service









Setup phase


Secret sharing is a fundamental technique upon which numerous advanced threshold cryptography mechanisms depend. It entails the division of a secret value 's' into 'n' shares (s1, s2, ..., sn), with the condition that the original secret 's' can only be reconstructed when a minimum threshold of 't' shares is presented.
Drand utilizes Feldman's VSS (Verifiable Secret Sharing) scheme, which safeguards against malicious actors by allowing participants to confirm that their received shares align with those distributed to other nodes. This verification process ensures that the shared secret can be accurately reconstructed in the future.

Drand leverages Pedersen's Distributed Key Generation (DKG) scheme, which operates multiple instances of Feldman's Verifiable Secret Sharing (VSS) in parallel, supplemented by additional verification steps.

Bilinearity Non-degeneracy Computability BLS12-381

Threshold Boneh-Lynn-Shacham (BLS) signatures encompass three essential components: key generation, signature generation, and signature verification, providing a comprehensive framework for secure and efficient cryptographic operations.

The pedersen-bls-chained scheme is designed to facilitate the chained mode, while either the pedersen-bls-unchained or bls-unchained-on-g1 scheme can be employed to support the unchained mode.
Beacon phase